Public key authentication has long been considered one of the most secure methods of remote SSH authentication. However, using the same key-pair for more than one machine can pose security risks, especially if that key is not secured by a passphrase but managing unique keys for each system a user has access to can be nightmare inducing. For this reason, we have leveraged Active Directory as our SSH public key store. For the purpose of this article, you should already have your Linux machines pulling user data from Active Directory, you should be running Windows Server 2012 R2 and you should have access to your domain `Administrator` user.
Extending the Active Directory Schema
1. Our first tasks is to extend the schema. First off, launch a `cmd` prompt then spawn an `Administrator` cmd by running:
runas /user:DOMAIN\Administrator cmd
[[image:Runas_Cmd.png|medium]]
2. Now run regedit in that prompt
3. In the Registry Editor, we need to enable Schema updates.
I. Browse to HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\NTDS\Parameters
II. Add a new DWORD key named `Schema Update Allowed` with value `1`
[[image:Edit_Registry_Enable_Schema_Updates.png|medium]]
4. Back in your Administrator command prompt, run regsvr32 schmmgmt.dll to enable the Schema Editor Snap-in.
[[image:Enable_Schema_Snapin.png|medium]]
5. Run `mmc` from the aforementioned Admin `cmd`
6. Hit Ctrl + M in the Management Console and add the Schema Editor
[[image:Schema_Snapin.png|medium]]
Now lets add the new Attribute:
I. Right Click on `Attributes` and click ‘Create New Attribute’
II. For ‘Common Name’ and ‘LDAP Display Name’, enter `sshPublicKeys`
III. For ‘Unique X500 Object ID’ enter `1.3.6.1.4.1.24552.1.1.1.13`
IV. For Syntax, select `IA5-String`
V. Check the ‘Multi-Valued’ box
VI. Minimum and Maximum can be left blank
[[image:https://blog.laslabs.com/user-files/uploads/2017/07/SSH_Key_Attribute.png|SSH Key Attribute|medium]]
We can now create a new class for the attribute:
I. Right click on `Classes` and click ‘Create class’
II. For ‘Common Name’ and ‘LDAP Display Name’, enter `ldapPublicKey`.
III. For ‘Unique X500 Object ID’ enter `1.3.6.1.4.1.24552.500.1.1.2.0`
IV. For `Parent Class` enter ‘top’ and for `Class Type` select ‘Auxiliary’.
[[image:Create_class.png|medium]]
Click next.
I. Under optional add `sshPublicKeys`
[[image:Create_class_II.png|medium]]
We can now associate that class to `user` objects.
I. Expand Classes and right click User then select properties.
II. Click on the `Relationship` tab then click `Add Class` under `Auxiliary class`
III. Add `ldapPublicKey` and click ‘Apply’
[[image:Assoc_Class.png|medium]]
Close all windows.
Now, open ADUC (dsa.mmc) and enabled Advanced Features
[[image:Enable_Advanced_ADUC.png|medium]]
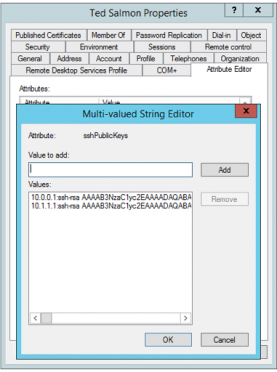
Once complete, browse to a user and select the ‘Attribute Editor’ tab. You will now be able to add public keys to this user.
[[image:sshPublicKeys.png|medium]]
From here, you should create a script to automatically pull public keys from AD for a given box and schedule it via Cron. Please remember to disable your domain `Administrator` account when you’re done!
Good luck!
Leave a Reply to frennkie Cancel reply